Looking to configure a Cisco switch for the first time? If the answer is YES, you’re in the right place. In this post, I’m going to show you how to configure a Cisco switch step-by-step.
Table of Contents
You’re going to configure:
Here’s a network diagram, so you can follow every step of the configuration.
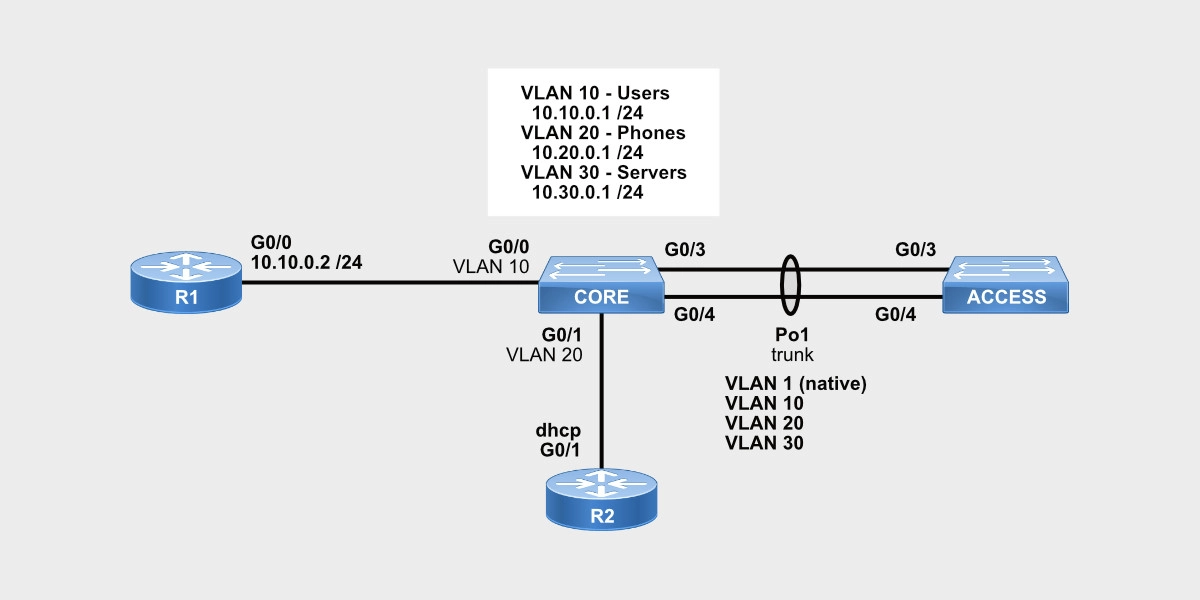
Let’s get started.
Advertisement
Virtual LANs (VLANs)
Virtual LANs, or VLANs, are a logical way to limit network traffic and prevent it from being propagated everywhere on the network where it doesn’t need to be.
There are three types of Ethernet traffic:
- Unicast: traffic directed to another Ethernet device specifically.
- Multicast: traffic directed to a specific group of Ethernet devices, a group for which those Ethernet devices signed up (i.e. a PC joining a TV channel).
- Broadcast: traffic directed to all Ethernet devices on the network.
A VLAN limits multicast and broadcast traffic. If a device belongs to VLAN 10 and generates a broadcast message, switches will forward that broadcast to all ports that belong to VLAN 10. Only devices on VLAN 10 will receive that broadcast message. Devices on VLAN 20 won’t receive that broadcast.
Here are the commands to configure two VLANs.
CORE#config term Enter configuration commands, one per line. End with CNTL/Z. CORE(config)#vlan 10 CORE(config-vlan)#name USERS CORE(config-vlan)#exit CORE(config)#vlan 20 CORE(config-vlan)#name PHONES CORE(config-vlan)#exit CORE(config)#vlan 30 CORE(config-vlan)#name SERVERS CORE(config-vlan)#exit CORE(config)#exit CORE# *Mar 8 14:09:40.404: %SYS-5-CONFIG_I: Configured from console by console CORE#
To verify VLANs already created, use the show vlan brief command.
CORE#show vlan brief *Mar 9 13:41:00.678: %SYS-5-CONFIG_I: Configured from console by console VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Gi0/0, Gi0/1, Gi0/2, Gi0/3 10 USERS active 20 PHONES active 30 SERVERS active 1002 fddi-default act/unsup 1003 token-ring-default act/unsup 1004 fddinet-default act/unsup 1005 trnet-default act/unsup CORE#
Now you have three VLANs on the VLAN database. Let’s assign Gigabit Ethernet interfaces to those VLANs.
Advertisement
Access & Trunk Ports
The difference between an access and a trunk port is that an access port belongs to a VLAN (untagged) whereas a trunk port can carry multiple VLANs (one untagged and the rest tagged).
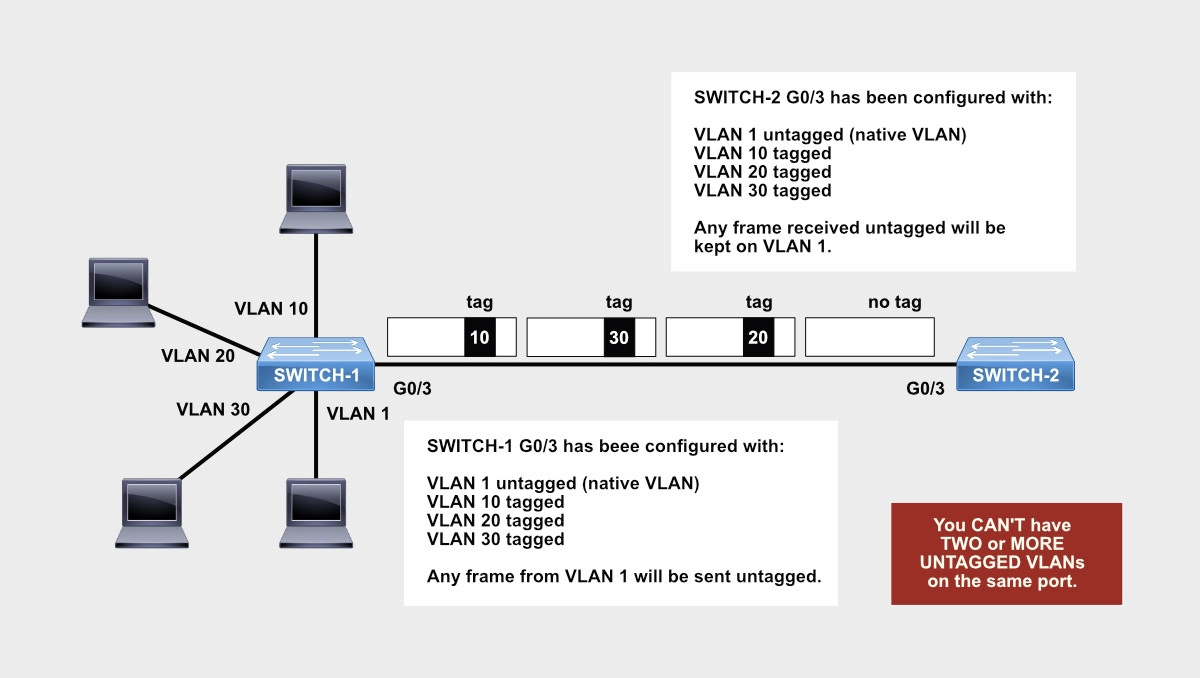
Let me elaborate.
VLAN tagging is an Ethernet concept. Ethernet’s units of information are called frames just like IP’s information units are called packets. Frames contain IP packets inside because of an encapsulation process. In other words, frames wrap around IP packets. When a computer sends an IP packet over an Ethernet network, the IP packet leaves the NIC card wrapped in an Ethernet frame. This frame is then carried, or switched, from one switch to another until it reaches its final destination within its own VLAN, and only within its own VLAN.
Since switches can have multiple VLANs configured, how can a switch tell another switch that a frame belongs to VLAN 10, 20, or 30? Well, the switch can put a mark on each frame called an 802.1Q tag. Inside this tag, the receiving switch can find the VLAN to which the Ethernet frame received belongs.
Since a switch can tag all of its VLANs over a trunk port, only one VLAN can remain untagged (the native VLAN); therefore, both switches must agree on what VLAN will be the native VLAN on the ports that interconnect both switches. By default, VLAN 1 is the untagged VLAN on a trunk port. All other VLANs get tagged.
All Cisco switches come from the factory with VLAN 1 preconfigured.
An access port belongs to one VLAN and this VLAN is untagged. Let’s configure two access ports, G0/0 on VLAN 10 and G0/1 on VLAN 20, on the CORE switch. Remember these VLANs were already created, so we’re now assigning physical interfaces to them.
CORE#config term Enter configuration commands, one per line. End with CNTL/Z. CORE(config)#interface gigabitEthernet 0/0 CORE(config-if)#switchport mode access CORE(config-if)#switchport access vlan 10 CORE(config-if)#spanning-tree portfast %Warning: portfast should only be enabled on ports connected to a single host. Connecting hubs, concentrators, switches, bridges, etc... to this interface when portfast is enabled, can cause temporary bridging loops. Use with CAUTION %Portfast has been configured on GigabitEthernet0/0 but will only have effect when the interface is in a non-trunking mode. CORE(config-if)#no shutdown CORE(config-if)#exit CORE(config)# CORE(config)# CORE(config)#interface gigabitEthernet 0/1 CORE(config-if)#switchport mode access CORE(config-if)#switchport access vlan 20 CORE(config-if)#spanning-tree portfast %Warning: portfast should only be enabled on ports connected to a single host. Connecting hubs, concentrators, switches, bridges, etc... to this interface when portfast is enabled, can cause temporary bridging loops. Use with CAUTION %Portfast has been configured on GigabitEthernet0/1 but will only have effect when the interface is in a non-trunking mode. CORE(config-if)#end CORE#
Let’s run some verifications.
CORE#show interfaces gigabitEthernet 0/0 switchport Name: Gi0/0 Switchport: Enabled Administrative Mode: static access Operational Mode: static access Administrative Trunking Encapsulation: negotiate Operational Trunking Encapsulation: native Negotiation of Trunking: Off Access Mode VLAN: 10 (USERS) Trunking Native Mode VLAN: 1 (default) Administrative Native VLAN tagging: enabled Voice VLAN: none Administrative private-vlan host-association: none Administrative private-vlan mapping: none Administrative private-vlan trunk native VLAN: none Administrative private-vlan trunk Native VLAN tagging: enabled Administrative private-vlan trunk encapsulation: dot1q Administrative private-vlan trunk normal VLANs: none Administrative private-vlan trunk associations: none Administrative private-vlan trunk mappings: none Operational private-vlan: none Trunking VLANs Enabled: ALL Pruning VLANs Enabled: 2-1001 Capture Mode Disabled Capture VLANs Allowed: ALL Protected: false Appliance trust: none CORE# CORE#show interfaces gigabitEthernet 0/1 switchport Name: Gi0/1 Switchport: Enabled Administrative Mode: static access Operational Mode: static access Administrative Trunking Encapsulation: negotiate Operational Trunking Encapsulation: native Negotiation of Trunking: Off Access Mode VLAN: 20 (PHONES) Trunking Native Mode VLAN: 1 (default) Administrative Native VLAN tagging: enabled Voice VLAN: none Administrative private-vlan host-association: none Administrative private-vlan mapping: none Administrative private-vlan trunk native VLAN: none Administrative private-vlan trunk Native VLAN tagging: enabled Administrative private-vlan trunk encapsulation: dot1q Administrative private-vlan trunk normal VLANs: none Administrative private-vlan trunk associations: none Administrative private-vlan trunk mappings: none Operational private-vlan: none Trunking VLANs Enabled: ALL Pruning VLANs Enabled: 2-1001 Capture Mode Disabled Capture VLANs Allowed: ALL Protected: false Appliance trust: none CORE#
A trunk port can carry multiple VLANs (one or more) and only one VLAN can be untagged. The rest of the VLANs have to be tagged. In addition, all ports come preconfigured in trunk auto mode with Dynamic Trunking Protocol (DTP). DTP defines the willingness of a port to establish a trunk when the port is linked up to another DTP port.
When you connect two switches together, DTP on those interconnecting ports will negotiate with the remote port to establish a trunk, so both ports auto-configure themselves as trunk ports. If DTP fails to negotiate, the port defaults to an access port.
I prefer to manually set up a trunk port as a trunk instead of leaving it up to DTP. Besides, even when you manually set up a port as a trunk, DTP still kicks in and adds extra time until the interface comes up. Because this delay is unnecessary, I recommend using the switchport nonegotiate command to disable DTP.
Quick note, when you configure an interface as an access port, DTP is disabled automatically.
Let’s configure G0/2 on both switches, CORE and ACCESS, as trunk ports and disable Dynamic Trunking Protocol.
CORE#configure terminal Enter configuration commands, one per line. End with CNTL/Z. CORE(config)#interface gigabitEthernet 0/2 CORE(config-if)#description ACCESS G0/2 CORE(config-if)#switchport mode trunk ! By default, all VLANs in the VLAN database are allowed CORE(config-if)#switchport nonegotiate CORE(config-if)#no shutdown CORE(config-if)#end CORE#
ACCESS#config term Enter configuration commands, one per line. End with CNTL/Z. ACCESS(config)#interface gigabitEthernet 0/2 ACCESS(config-if)#description CORE G0/2 ACCESS(config-if)#switchport mode trunk ! By default, all configured VLANs are allowed ACCESS(config-if)#switchport nonegotiate ACCESS(config-if)#no shut ACCESS(config-if)#exit ACCESS(config)#end ACCESS#
Let’s run some verification commands.
CORE#show interfaces gigabitEthernet 0/2 switchport Name: Gi0/2 Switchport: Enabled Administrative Mode: trunk Operational Mode: trunk Administrative Trunking Encapsulation: dot1q Operational Trunking Encapsulation: dot1q Negotiation of Trunking: Off <<<<<< DTP is disabled Access Mode VLAN: 1 (default) Trunking Native Mode VLAN: 1 (default) <<<<<< Native VLAN is VLAN 1 Administrative Native VLAN tagging: enabled Voice VLAN: none Administrative private-vlan host-association: none Administrative private-vlan mapping: none Administrative private-vlan trunk native VLAN: none Administrative private-vlan trunk Native VLAN tagging: enabled Administrative private-vlan trunk encapsulation: dot1q Administrative private-vlan trunk normal VLANs: none Administrative private-vlan trunk associations: none Administrative private-vlan trunk mappings: none Operational private-vlan: none Trunking VLANs Enabled: ALL <<<<<< All VLANs are trunked Pruning VLANs Enabled: 2-1001 Capture Mode Disabled Capture VLANs Allowed: ALL Protected: false Appliance trust: none CORE#
ACCESS#show interfaces gigabitEthernet 0/2 switchport Name: Gi0/2 Switchport: Enabled Administrative Mode: trunk Operational Mode: trunk Administrative Trunking Encapsulation: dot1q Operational Trunking Encapsulation: dot1q Negotiation of Trunking: Off Access Mode VLAN: 1 (default) Trunking Native Mode VLAN: 1 (default) Administrative Native VLAN tagging: enabled Voice VLAN: none Administrative private-vlan host-association: none Administrative private-vlan mapping: none Administrative private-vlan trunk native VLAN: none Administrative private-vlan trunk Native VLAN tagging: enabled Administrative private-vlan trunk encapsulation: dot1q Administrative private-vlan trunk normal VLANs: none Administrative private-vlan trunk associations: none Administrative private-vlan trunk mappings: none Operational private-vlan: none Trunking VLANs Enabled: ALL Pruning VLANs Enabled: 2-1001 Capture Mode Disabled Capture VLANs Allowed: ALL Protected: false Appliance trust: none ACCESS#
By default, all VLANs are allowed through the trunk; however, you can limit what VLANs can traverse the trunk interface. If the ACCESS switch only has users on VLAN 10 and VLAN 1 is being used for management, for example, you can only allow VLANs 1 and 10 through the trunk interface.
CORE#configure terminal Enter configuration commands, one per line. End with CNTL/Z. CORE(config)#interface gigabitEthernet 0/2 CORE(config-if)#description ACCESS G0/2 CORE(config-if)#switchport mode trunk CORE(config-if)#switchport trunk allowed vlan 1,10 CORE(config-if)#no shutdown CORE(config-if)#end CORE#
Let’s verify.
CORE#show interfaces gigabitEthernet 0/2 switchport Name: Gi0/2 Switchport: Enabled Administrative Mode: trunk Operational Mode: trunk Administrative Trunking Encapsulation: dot1q Operational Trunking Encapsulation: dot1q Negotiation of Trunking: Off Access Mode VLAN: 1 (default) Trunking Native Mode VLAN: 1 (default) Administrative Native VLAN tagging: enabled Voice VLAN: none Administrative private-vlan host-association: none Administrative private-vlan mapping: none Administrative private-vlan trunk native VLAN: none Administrative private-vlan trunk Native VLAN tagging: enabled Administrative private-vlan trunk encapsulation: dot1q Administrative private-vlan trunk normal VLANs: none Administrative private-vlan trunk associations: none Administrative private-vlan trunk mappings: none Operational private-vlan: none Trunking VLANs Enabled: 1,10 Pruning VLANs Enabled: 2-1001 Capture Mode Disabled Capture VLANs Allowed: ALL Protected: false Appliance trust: none CORE#
Let’s undo this for now and allow all the VLANs. Just know that you can allow certain VLANs on the trunk.
CORE#config term CORE(config)#interface gigabitEthernet 0/2 CORE(config-if)#no switchport trunk allowed vlan 1,10 CORE(config-if)#end CORE#
So, the final configuration on CORE G0/2 is:
CORE#show running-config interface gigabitEthernet 0/2 Building configuration... Current configuration : 168 bytes ! interface GigabitEthernet0/2 switchport mode trunk switchport nonegotiate negotiation auto end CORE#
And the final configuration on ACCESS G0/2 is:
ACCESS#show running-config interface gigabitEthernet 0/2 Building configuration... Current configuration : 168 bytes ! interface GigabitEthernet0/2 switchport mode trunk switchport nonegotiate negotiation auto end ACCESS#
Now that we have configured access and trunk ports, let’s configure VLAN interfaces, also known as Switched VLAN Interfaces (SVIs).
Advertisement
VLAN Interfaces (SVIs)
A Layer 3 Switch has routing capabilities. Think of it as an Ethernet switch with an internal router off of which you can extend routed interfaces to each of the VLANs. Each of those virtual interfaces becomes a Switched Virtual Interface, or SVI, for the VLAN it was assigned to.
On a Layer 3 Switch, a VLAN interface, or SVI, is a virtual interface that’s part of a VLAN and to which can be assigned an IP address for routing purposes. Normally, a VLAN interface becomes the default gateway for the subnet associated with that VLAN. The IP address configured on the SVI defines the subnet on the VLAN.
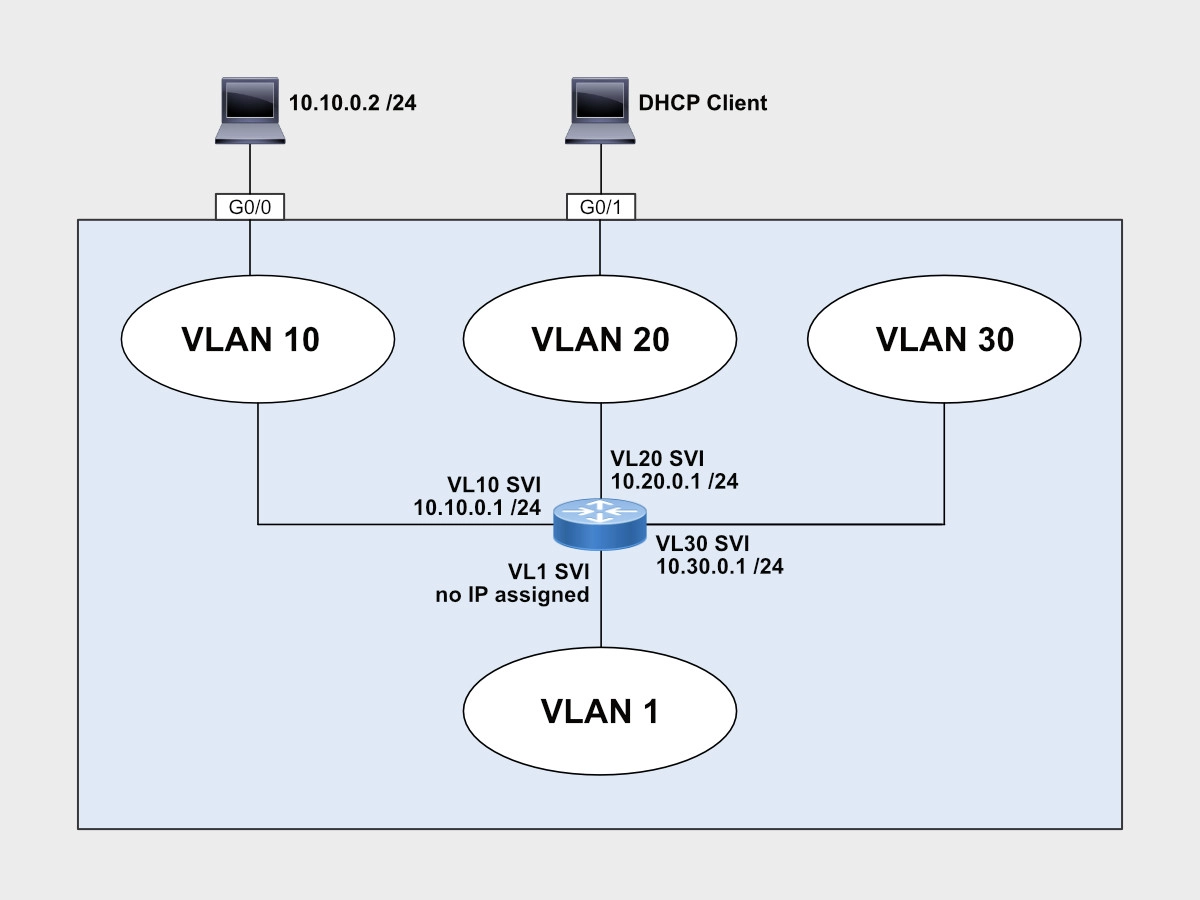
Each physical interface can be assigned to a VLAN in the form of an access port or multiple VLANs as a trunk port.
Let’s configure VLAN interfaces on the CORE switch.
CORE#config term Enter configuration commands, one per line. End with CNTL/Z. CORE(config)#interface vlan 10 CORE(config-if)#description USERS <<<<<< Optional but recommended CORE(config-if)#ip address 10.10.0.1 255.255.255.0 CORE(config-if)#no ip redirects <<<<<< Optional but recommended CORE(config-if)#no ip unreachables <<<<<< Optional but recommended CORE(config-if)#no ip proxy-arp <<<<<< Optional but recommended CORE(config-if)#no shutdown CORE(config-if)#exit CORE(config)# CORE(config)#interface vlan 20 CORE(config-if)#description PHONES CORE(config-if)#ip address 10.20.0.1 255.255.255.0 CORE(config-if)#no ip redirects CORE(config-if)#no ip unreachables CORE(config-if)#no ip proxy-arp CORE(config-if)#no shutdown CORE(config-if)#exit CORE(config)# CORE(config)#interface vlan 30 CORE(config-if)#description SERVERS CORE(config-if)#ip address 10.30.0.1 255.255.255.0 CORE(config-if)#no ip redirects CORE(config-if)#no ip unreachables CORE(config-if)#no ip proxy-arp CORE(config-if)#no shutdown CORE(config-if)#end CORE#
Let’s verify.
CORE#show ip interface brief | ex unass <<<<<< exclude any line that contains unass
Interface IP-Address OK? Method Status Protocol
Vlan10 10.10.0.1 YES manual up up
Vlan20 10.20.0.1 YES manual up up
Vlan30 10.30.0.1 YES manual up up
CORE#
CORE#show ip route connected
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
Gateway of last resort is not set
10.0.0.0/8 is variably subnetted, 6 subnets, 2 masks
C 10.10.0.0/24 is directly connected, Vlan10
L 10.10.0.1/32 is directly connected, Vlan10
C 10.20.0.0/24 is directly connected, Vlan20
L 10.20.0.1/32 is directly connected, Vlan20
C 10.30.0.0/24 is directly connected, Vlan30
L 10.30.0.1/32 is directly connected, Vlan30
CORE#
Now, R1 is connected to an access port on VLAN 10. Let’s see if we can ping VLAN 10’s SVI.
R10#show running-config interface gigabitEthernet 0/0 Building configuration... Current configuration : 114 bytes ! interface GigabitEthernet0/0 ip address 10.10.0.2 255.255.255.0 duplex auto speed auto media-type rj45 end R10#ping 10.10.0.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.10.0.1, timeout is 2 seconds: .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 28/37/43 ms R10#
Yes. From R10, we can ping CORE’s VLAN 10 SVI.
Advertisement
DHCP Server
Cisco IOS switches can be configured as DHCP Servers to provide IP addresses and other IP settings to DHCP Clients. In our topology, R2 was been configured as a DHCP Client.
Let’s configure a DHCP pool of IP addresses that the CORE switch can use to assign IP addresses to DHCP clients on VLAN 20.
CORE#config term Enter configuration commands, one per line. End with CNTL/Z. CORE(config)# CORE(config)#ip dhcp excluded-address 10.20.0.1 10.20.0.10 CORE(config)#ip dhcp pool VLAN20 CORE(dhcp-config)#network 10.20.0.0 /24 CORE(dhcp-config)#default-router 10.20.0.1 CORE(dhcp-config)#dns 8.8.8.8 4.2.2.2 CORE(dhcp-config)#end CORE#
Let’s enable R20 to obtain an IP address via DHCP protocol on its Gi0/0 interface, the interface connected to the CORE switch’s Gi0/1 interface assigned to VLAN 20.
R20#confi term Enter configuration commands, one per line. End with CNTL/Z. R20(config)#interface gigabitEthernet 0/0 R20(config-if)#ip address dhcp R20(config-if)#no shutdown R20(config-if)#no ip redirects R20(config-if)#no ip unreachables R20(config-if)#no ip proxy-arp R20(config-if)# *Mar 10 13:19:09.029: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/0, changed state to up *Mar 10 13:19:21.672: %DHCP-6-ADDRESS_ASSIGN: Interface GigabitEthernet0/0 assigned DHCP address 10.20.0.11, mask 255.255.255.0, hostname R20 R20(config-if)#end R20# R20#show ip interface brief Interface IP-Address OK? Method Status Protocol GigabitEthernet0/0 10.20.0.11 YES DHCP up up GigabitEthernet0/1 unassigned YES NVRAM administratively down down GigabitEthernet0/2 unassigned YES NVRAM administratively down down GigabitEthernet0/3 unassigned YES NVRAM administratively down down R20#
Notice the log message on R20 saying that 10.20.0.11 was assigned. Let’s verify on the CORE switch.
CORE#show ip dhcp binding
Bindings from all pools not associated with VRF:
IP address Client-ID/ Lease expiration Type State Interface
Hardware address/
User name
10.20.0.11 0063.6973.636f.2d35. Mar 11 2022 01:20 PM Automatic Active Vlan20
3235.342e.3030.3061.
2e30.3733.352d.4769.
302f.30
CORE#
Let’s make sure that R20 can ping the CORE switch.
R20#ping 10.20.0.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.20.0.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 38/56/75 ms R20#
If you have multiple pools with different subnets, how does the switch know what pool to use for each VLAN 20? The IP subnet and mask on the VLAN interfaces need to match the subnet configured on the DHCP pool.
We have an ACCESS switch with two interfaces connected to the CORE switch. How can we combine two or more interfaces into one single logical interface? Let’s take a look at how we can do this.
Advertisement
Port Channel Interfaces
Port Channels are a technology that allows network devices to combine two or more physical interfaces into one single logical interface. On the device, when an IP packet needs to exit the port channel, each IP packet is run through a hash algorithm to decide what physical interface the IP packet will be sent to. If one physical interface fails, all of its traffic is redirected over the remaining physical interfaces bundled by the port channel.
On our diagram, notice that CORE G0/2 and G0/3 are connected to ACCESS G0/2 and G0/3, respectively. We already configured G0/2 as a trunk interface, but now we’re going to configure G0/3 as a trunk interface, and then we’re going to combine G0/2 and G0/3 into Port Channel 1 (Po1). Po1 will also be configured as a trunk port so all VLANs can pass through it.

CORE#show runn interface g0/2 Building configuration... Current configuration : 115 bytes ! interface GigabitEthernet0/2 switchport mode trunk negotiation auto end CORE#config term Enter configuration commands, one per line. End with CNTL/Z. CORE(config)#interface gigabitEthernet 0/3 CORE(config-if)#switchport mode trunk CORE(config-if)#switchport nonegotiate CORE(config-if)#no shutdown CORE(config-if)#exit CORE(config)# CORE(config)#interface port-channel 1 CORE(config-if)#switchport mode trunk CORE(config-if)#switchport nonegotiate CORE(config-if)#no shutdown CORE(config-if)#exit CORE(config)# CORE(config)#interface range g0/2-3 CORE(config-if-range)#channel-group 1 mode active CORE(config-if-range)#exit CORE(config)# CORE(config)#interface port-channel 1 CORE(config-if)#shutdown CORE(config-if)#exit CORE(config)#
I shut down port-channel 1, which in turn shuts down its member interfaces G0/2 and G0/3. I shut down port-channel 1 because the port channel on the ACCESS switch has not been configured yet. Let’s configure the port channel on the ACCESS switch now.
ACCESS#show running-config interface g0/2
Building configuration...
Current configuration : 115 bytes
!
interface GigabitEthernet0/2 <<<<<< Gi0/2 is already configured as a trunk with DTP disabled
switchport mode trunk
switchport nonegotiate
negotiation auto
end
ACCESS#
ACCESS#config term
Enter configuration commands, one per line. End with CNTL/Z.
ACCESS(config)#interface gigabitEthernet 0/3
ACCESS(config-if)#switchport mode trunk
ACCESS(config-if)#switchport nonegotiate
ACCESS(config-if)#no shut
ACCESS(config-if)#exit
ACCESS(config)#
ACCESS(config)#
ACCESS(config)#interface port-channel 1
ACCESS(config-if)#switchport mode trunk
ACCESS(config-if)#switchport nonegotiate
ACCESS(config-if)#no shutdown
ACCESS(config-if)#exit
ACCESS(config)#
ACCESS(config)#interface range g0/2-3
ACCESS(config-if-range)#channel-group 1 mode active
ACCESS(config-if-range)#no shutdown
ACCESS(config-if-range)#
ACCESS#
ACCESS#
ACCESS#show etherchannel summary
Flags: D - down P - bundled in port-channel
I - stand-alone s - suspended
H - Hot-standby (LACP only)
R - Layer3 S - Layer2
U - in use N - not in use, no aggregation
f - failed to allocate aggregator
M - not in use, minimum links not met
m - not in use, port not aggregated due to minimum links not met
u - unsuitable for bundling
w - waiting to be aggregated
d - default port
A - formed by Auto LAG
Number of channel-groups in use: 1
Number of aggregators: 1
Group Port-channel Protocol Ports
------+-------------+-----------+-----------------------------------------------
1 Po1(SU) LACP Gi0/2(P) Gi0/3(P)
ACCESS#
Let’s bring up and check the port channel on the CORE switch side now.
CORE#config term
Enter configuration commands, one per line. End with CNTL/Z.
CORE(config)#
CORE(config)#interface port-channel 1
CORE(config-if)#no shutdown
CORE(config-if)#end
CORE#
CORE#show etherchannel summary
Flags: D - down P - bundled in port-channel
I - stand-alone s - suspended
H - Hot-standby (LACP only)
R - Layer3 S - Layer2
U - in use N - not in use, no aggregation
f - failed to allocate aggregator
M - not in use, minimum links not met
m - not in use, port not aggregated due to minimum links not met
u - unsuitable for bundling
w - waiting to be aggregated
d - default port
A - formed by Auto LAG
Number of channel-groups in use: 1
Number of aggregators: 1
Group Port-channel Protocol Ports
------+-------------+-----------+-----------------------------------------------
1 Po1(SU) LACP Gi0/2(P) Gi0/3(P)
CORE#
(P) is what we want to see. P means “bundled in port-channel.”
By default, all the VLANs are allowed through. VLAN 1 is the untagged or native VLAN, and all the other VLANs are tagged.
CORE#show interfaces port-channel 1 switchport Name: Po1 Switchport: Enabled Administrative Mode: trunk Operational Mode: trunk Administrative Trunking Encapsulation: dot1q Operational Trunking Encapsulation: dot1q Negotiation of Trunking: Off Access Mode VLAN: 1 (default) Trunking Native Mode VLAN: 1 (default) Administrative Native VLAN tagging: enabled Voice VLAN: none Administrative private-vlan host-association: none Administrative private-vlan mapping: none Administrative private-vlan trunk native VLAN: none Administrative private-vlan trunk Native VLAN tagging: enabled Administrative private-vlan trunk encapsulation: dot1q Administrative private-vlan trunk normal VLANs: none Administrative private-vlan trunk associations: none Administrative private-vlan trunk mappings: none Operational private-vlan: none Trunking VLANs Enabled: ALL Pruning VLANs Enabled: 2-1001 Protected: false Appliance trust: none CORE#
Since our CORE switch has IP addresses configured on VLAN interfaces, it can be accessed remotely for configuration and management. Let’s lock down that access with SSH and local authentication.
Advertisement
SSH Access with Local AAA Authentication
AAA stands for authentication, authorization, and accounting.
- Authentication is about determining identity. Who are you?
- Authorization is about defining what individuals or groups of identities can do. What can you do? What can you access?
- Accounting is about keeping track of what individual identities have done. What did you do? How long did you do it? How often did you do it?
AAA data must be stored either locally on the routers or switches or on a centralized AAA server. The simplest implementation is to use the local database on individual network devices, which means that AAA authentication and authorization data are stored directly in the device’s configuration.
During local authentication, the user establishes a connection with the router or switch and the router or switch prompts the user for a username and password, authenticating the user using a local database.
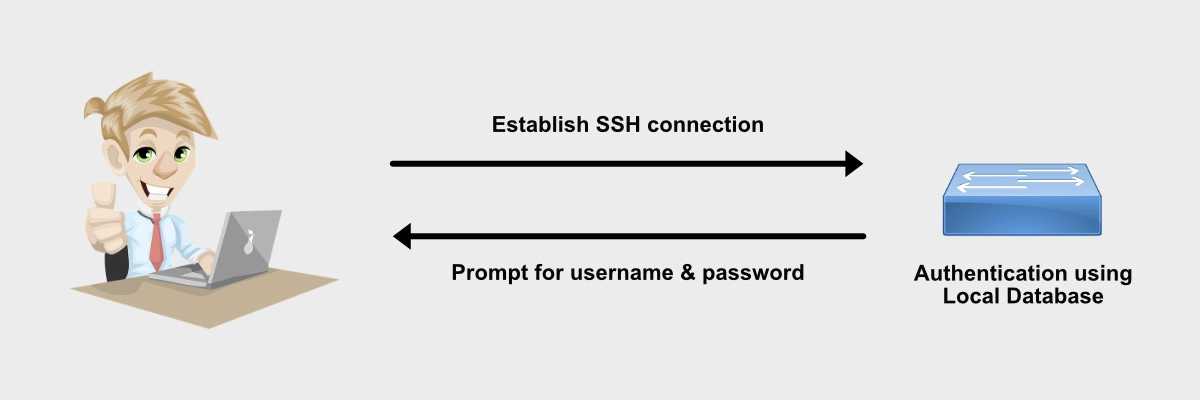
CORE#config term CORE(config)#aaa new-model CORE(config)#aaa authentication login default local CORE(config)#aaa authorization exec default local CORE(config)# CORE(config)#username adminuser privilege 15 secret P4$$w0RD CORE(config)# CORE(config)#enable secret 3n4BL3p@sS CORE(config)#
Secure Socket Shell (SSH) is a network protocol that allows you to securely access and communicate with remote devices. SSH provides strong encryption and is widely used by network administrators and developers to manage remote systems & applications, execute commands, share files, etc.
RSA (Rivest–Shamir–Adleman) is a public-key cryptosystem that is widely used for secure data transmission. RSA is an algorithm used by modern computers to encrypt and decrypt messages.
On Cisco routers and switches, SSH requires an RSA key pair created. Here are the steps:
- Give a hostname
- Give a domain name
- Create RSA public-private key pair
CORE#config term Enter configuration commands, one per line. End with CNTL/Z. CORE(config)#hostname CORE <<<<<< Already given to this router but re-added here for clarity CORE(config)# CORE(config)#ip domain name howtorouteswitch.com CORE(config)# CORE(config)#crypto key generate rsa general-keys modulus ? <360-4096> size of the key modulus [360-4096] CORE(config)#crypto key generate rsa general-keys modulus 2048 The name for the keys will be: CORE.howtorouteswitch.com % The key modulus size is 2048 bits % Generating 2048 bit RSA keys, keys will be non-exportable... [OK] (elapsed time was 25 seconds) CORE(config)#exit CORE#
Let’s test SSH access into the CORE switch from R10.
R10#ping 10.10.0.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.10.0.1, timeout is 2 seconds: .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 26/50/76 ms R10# R10#ssh -l adminuser 10.10.0.1 IOSv - Cisco Systems Confidential - Supplemental End User License Restrictions This IOSv software is provided AS-IS without warranty of any kind. Under no circumstances may this software be used separate from the Cisco Modeling Labs Software that this software was provided with, or deployed or used as part of a production environment. By using the software, you agree to abide by the terms and conditions of the Cisco End User License Agreement at http://www.cisco.com/go/eula. Unauthorized use or distribution of this software is expressly prohibited. Password: IOSv - Cisco Systems Confidential - Supplemental End User License Restrictions This IOSv software is provided AS-IS without warranty of any kind. Under no circumstances may this software be used separate from the Cisco Modeling Labs Software that this software was provided with, or deployed or used as part of a production environment. By using the software, you agree to abide by the terms and conditions of the Cisco End User License Agreement at http://www.cisco.com/go/eula. Unauthorized use or distribution of this software is expressly prohibited. CORE# <<<<<< I AM NOW ON THE CORE SWITCH
And wah-lah! I’m on the CORE switch.
Getting CCNA or CCNP Certified?

Self-paced Books. On-demand Courses. Practice Tests.
Sign up for a 10-day free trial with unlimited access!
Summary
In this post, we covered the basic configuration steps to get a Cisco switch going. These steps involved configuring:
- VLANs
- Access and Trunk Ports
- VLAN Interfaces or SVIs
- A DHCP Server
- Port Channel Interfaces
- SSH Access with Local AAA Authentication
I hope this post was informative for you. Please, leave your comments or questions below.
Thank you for reading.

Dear Sir,
Thank you very much for this informative and sensitive information, i hope to see more.
Thank you, Sensee!
Dear Sir
I’m currently studying for my ccna and i was just serching google and i got your website this is the best info. I’m from South africa can u guide the best way to learn CCNA to Level of CCNP.
Hey Joseph. Thanks for visiting. Please check my post: https://howtorouteswitch.com/pass-ccna/ and take a look at the video and book options I list in there. I also think that Internetwork Expert’s basic subscription at INE.com gives you access to CCNA training. Take care of your CCNA cert first, and then worry about your CCNP. One step at a time.
thank u i m interested with your web site there is many enginenring who want to knows to configuration cisco.i m from burundi
Hi Yves. Thanks for your feedback.